Home Office: securing the new remote work
Since the Corona crisis held the world ransom, the number of remote workers has exploded and security managers have been faced with the task of ensuring that operations run as smoothly as possible. The fact that numerous SaaS applications such as Office 365, Google Suite or Salesforce have already paved the way towards the home office by enabling collaboration and data sharing, regardless of location, has certainly helped get employees working. However, in the first phase of this mass rollout of home offices, security concerns were often put on the back burner. With most of the immediate technical requirements met, with workers being productive from home, the focus must now shift to ensuring that security standards are not dropping. Indeed, malicious actors are already organised to make the most of the new set up, so there is no room to delay.
No more protective company walls
IT infrastructures are in the midst of profound changes due to cloud-based applications. In the past, it was possible to clearly separate and distinguish between “outside” and “inside”, but this separation no longer exists. The perimeter is becoming increasingly blurred. Or, as Gartner puts it, “the perimeter is now wherever an organization needs it to be – a dynamically created, policy-based Secure Access Service Edge (SASE)”. Today, the enterprise data center is no longer the core of access requirements for users and devices. Instead, there are more and more users and data outside the enterprise, and employees are using more and more resources and applications outside the enterprise network. So the perimeter is no longer a rigid boundary, but a (dynamic) inter-relation between users, data and applications. Accordingly, traditional security solutions can no longer provide adequate protection. Ultimately, only a native cloud architecture can provide seamless security services in this world of extensive cloud adoption.
The SASE approach consolidates network and Security-as-a-Service capabilities into a low-latency solution delivered from the cloud that can analyze and understand data and correlations to apply policies to users, devices and services in the cloud. This includes Secure Web Gateway (SWG) capabilities alongside other cloud-delivered network and security services such as Cloud Access Security Broker (CASB), Data Loss Prevention (DLP), Advanced Threat Protection (ATP) and Zero Trust Network Access (ZTNA). Only through such a deeper set of security controls you can gain better visibility into activities across SaaS, Web, and IaaS services and across managed and unmanaged devices.
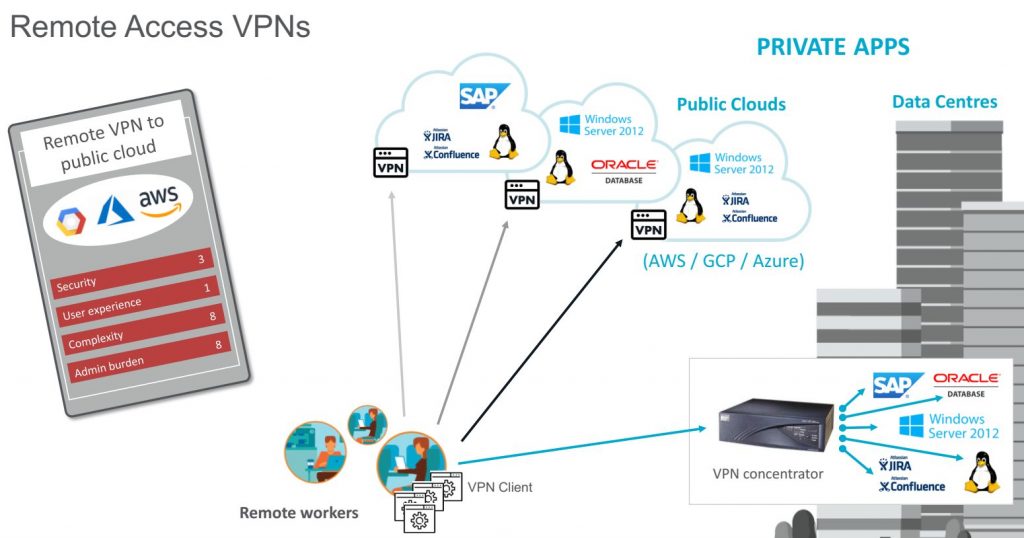
Zero Trust instead of VPN
Currently, most mobile employees and remote workers are connected to the corporate network via VPN. However, this has some disadvantages: VPNs only allow point-to-point access via the network, which is blind to applications and slows down processes for employees and business partners. In addition, VPN appliances are not scalable, are difficult to manage and cause growing maintenance costs. Finally, these do not offer up-to-date protection: the traditional “open” network access of VPNs makes it easy to exfiltrate sensitive data and allows compromised accounts or (malicious) insiders to move laterally within the network. In contrast, Zero Trust Network Access, as part of the comprehensive SASE approach, enables secure access by remote users to select private applications in public clouds and data centers regardless of location. This includes authenticating users and verifying and classifying device status before connecting users to the defined private applications.
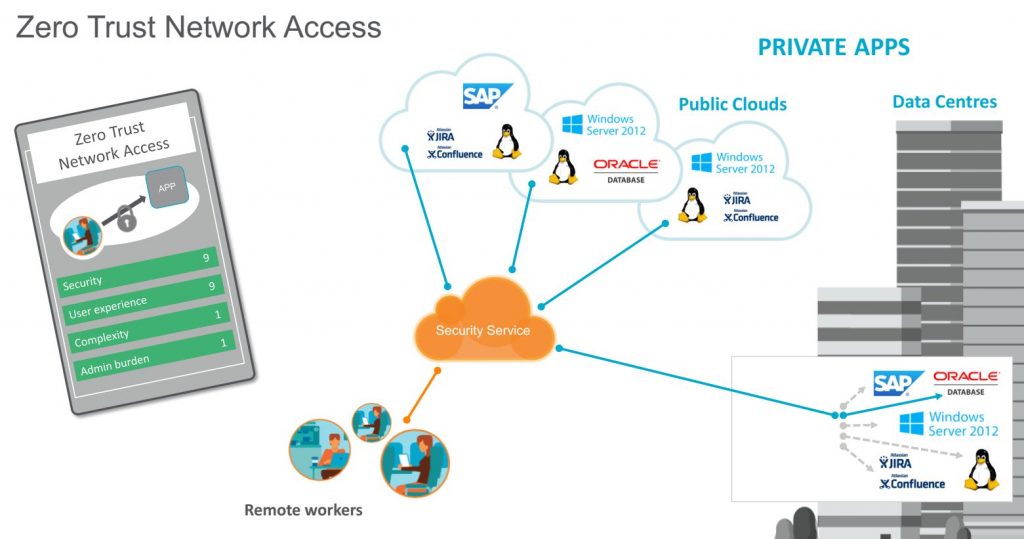
At a time when, according to the Netskope Cloud and Threat Report 2020, nine out of ten corporate users are in the cloud and actively use at least one cloud app every day, it ultimately makes little difference from where this access originates – be it the home office or a regular office on the corporate premises, assuming that the security strategy is generally designed for cloud utilization. Effective control of the movement of sensitive data through contextual controls and a data-centric security model is key. Regardless of the endpoint or cloud service, policies are applied and enforced, data is effectively identified and classified, and context (such as user, device type, file type, or data identifiers) is always incorporated. By adopting a SASE architecture, enterprises are much better protected against emerging threats and are able to meet data protection and data security requirements in the future – no matter where the workstation is located.
Thomas Ehrlich
Since September 2019, Thomas Ehrlich has been responsible for the growth and positioning of Netskope, serving as Regional Director DACH and Eastern Europe.
Most recently, Ehrlich was Country Manager DACH and Eastern Europe at Varonis, where he was responsible for positioning the company as an innovation and opinion leader and significantly expanded the market presence of the data security specialist. Before joining Varonis, he held various positions at NetApp, most recently as Vice President Global Accounts and Pathway Ecoysystem, where he was responsible for the EMEA channel and the management of the global accounts with headquarters in EMEA. Prior to that, as Vice President Pathways & Operations EMEA, he was responsible for the company's entire EMEA channel.
Ehrlich joined NetApp in 1999. Since then, he has held various management positions, initially as Sales Manager CE, Sales Manager Austria, Switzerland and Eastern Europe and Director Sales GEO Central Europe. In 2006, he was appointed Area Vice President Northeast EMEA, followed by Area Vice President South & Northeast EMEA in 2008.
Thomas Ehrlich studied Business Informatics in Munich before joining NetApp. He worked as a Systems Engineer and Channel Marketing Manager DACH at Silicon Graphics in Munich.


It seems to me that working from home is much more convenient if not mention cyber security. It’s much harder to protect the information, especially nowadays, when hackers try to steal all possible information online. I’ve found some steps how to secure yourself https://utopia.fans/security/cybersecurity-issues-with-remote-work-during-coronavirus/ but it seems that none of them can really give you 100% chance to stay safe online.