Cybersecurity Careers: Understanding the Space and Opportunities
With the given demand for cybersecurity professionals in the market, it is essential to understand the space and potential career. In this article we will discuss the overall cybersecurity career space from a birds-eye view.
Usually what one normally hears regarding cybersecurity career is associated to white hacking but there is much more in the cybersecurity space besides identifying the security issues. Given the space in which cybersecurity plays a role, we will look from holistic perspective at a high level in this article thus making this an umbrella article for the space of cybersecurity career.
Overall picture of cybersecurity is given in the figure below. We have divided potential cybersecurity career in several parts (1) cybersecurity areas or areas that forms core of cybersecurity; (2) associated areas, i.e., those that are related to cybersecurity and can be part of it or not depending on the organization; (3) technology specific career paths in cybersecurity such as security for operational technology (OT), internet of things (IoT) security or application security; (4) associated activities are those that relate to cybersecurity such as research in the field of cybersecurity or training activities that also have cybersecurity as part of it and (5) career paths that can be as a technical expert, management role or even leadership role that not necessarily involves management and security audit within the company. We will highlight the cybersecurity areas in this article from perspective of complete lifecycle of a product be it a network, software or hardware product.
In this article our focus is on cybersecurity areas since these forms the base for any other parts of potential career in cybersecurity.
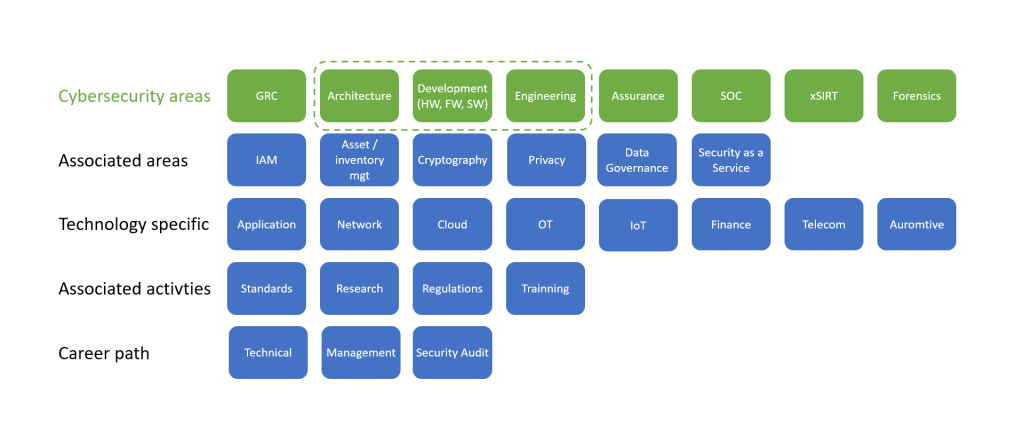
Cybersecurity Areas
As mentioned earlier, in this article our focus is on specific cybersecurity career areas shown in green in the figure. Rest of the potential career paths will not be covered in this article and are given for information only.
Governance, Risk and Compliance (GRC): The governance part of this career path is to develop security controls and see to its implementation. This also involves considering business risk for the company as wells as compliance against company rules and regulatory requirements. The activities of GRC are to develop policies for the company such as high-level security requirements, these policies are detailed in the form of process and then further detailed in procedures under architecture, implementation, or operations teams. The policies and process include all aspects of the company such as password policies, human resource, procurement, physical security etc. and their enforcement. One of the tasks of this career path is also to take care of security awareness and another one is to take care of security certifications as required by the company.
Architecture, Development & Engineering: We have bundled the 3 items together although they might exist separately depending on various factors including product and development methodology. The career path here is associated to secure product development to deployment and operations of the product (engineering). In this career path one must take care that security requirements are embedded as product requirement, development is done based on secure development policies and product is deployed in a secure fashion taking care of security policies for deployment. Once deployed, those in engineering team career path should also take care of continuous maintenance of the product be it update, upgrade, patching or issues in product or modification of configurations during operations.
Assurance: This career path is associated to various forms of security testing and could be split in different groups within given organization such as SOC or red team. Activities expected here are vulnerability assessment that can be done by analyzing the architecture, using tools to test against requirements or performing fuzz tests. Vulnerability assessment is often also associated to hardening preferably performed before deployment. Activities can also include continuous vulnerability assessment of a production network including configuration checks. In addition, security assurance task also involves penetration testing, or pentest, which is more of a white hacking activity of a product as well as existing network. Besides these activities, in this career path one could also get into source code analysis that requires tools and experience in identifying real issues. Continuous security as part of CI/CD pipeline, or DevSecOps, would also overlap with security assurance career path.
Security Operations Center (SOC): As the name says, a SOC is a center involving several roles and thus various career paths can be considered here. In essence task of a SOC is to monitor all assets of a company and respond to any incidence. Generic career paths in SOC are discussed here but they can also vary depending on the organization (1) threat hunting where one utilizes threat intelligence to find potential attacks to the organization, the task can be done with various tools but human expertise is very much required. (2) SOC could also have a network simulation to perform scenario-based attacks to identify any threat early on. Results of these studies are then developed into playbooks which are used for incidence response. (3) Analysts and incidence response activity requires people who can identify that an incidence has happened and then respond to it accordingly. The task would include identifying any attack based on numerous data showed by tools of a SOC, confirming it is an incidence and then performing activities to respond to it – there is more to how this is done. (4) Scripting and automation solution development is another task that is often done in SOC. (5) Various tools (such as SIEM, SOAR, xDR etc.) are used in SOC, these tools require maintenance and thus expertise is required for specific tools being used by a given SOC.
x Security Incidence and Response Team (CSIRT or PSIRT): There are two types (1) Computer security incident response team (CSIRT) and (2) product security incident response team (PSIRT). A CSIRT team takes care of incidence within an organization. This team works hand in hand with all parts of the organization taking in account incidence related to SOC or also those such as lost laptops. Depending on the criticality of the incidence the CSIRT will take actions as simple as informing all parties to take care of certain issues to alerting company executives to act. CSIRT also interfaces with external organizations such as police, regulators, CSIRTs in similar or related industries and media. A PSIRT on the other hand is associated to product developed by a company. The activity of a PSIRT is to continuously check any vulnerability associated to components of a product and accordingly take action that could involve informing customers regarding identified security issues.
Forensics: It might be necessary to find the reason regarding a given attack and take criminal actions. To do so, one has to perform forensics. The task requires collecting all evidence and analyzing how the given attack happened. There are various requirements for forensics since a change in state or tampering of evidence would lead to wrong conclusions.
Additional Career Paths and Conclusions
There are several other career paths associated to cybersecurity such as (1) Identity and access management where all assets of an organization should be identifiable and access controlled – although sounds simple, this is complex to achieve, (2) Privacy is becoming more and more critical with regulations appearing in all parts of the world thus it is becoming important for all organizations to take care of any kind of data that can lead to privacy issues. (3) Associated to privacy is also data governance that provides guidelines and takes care of policies on how data should be used by a given organization.
Given roles of cybersecurity can also be technology specific. One can consider developing in career as security expert for applications, IT networks, mobile networks, cloud, automotive etc.
Other areas where one can develop security career are (1) standards, where a person gets involved in international or national standardization bodies to define security specifications, (2) research of new solutions or even potential attacks, (3) regulatory relations or even security regulations development and (4) develop and provide security trainings.
For all the above, career path can be to grow as a technical person in a security team, be part of an internal audit team or audit company or grow in management path towards becoming a CISO.
Cybersecurity is a wide area given that it is required for all aspects of digitalization that we are seeing around us. With all the challenges, cybersecurity remains a very interesting career path to consider and grow.

